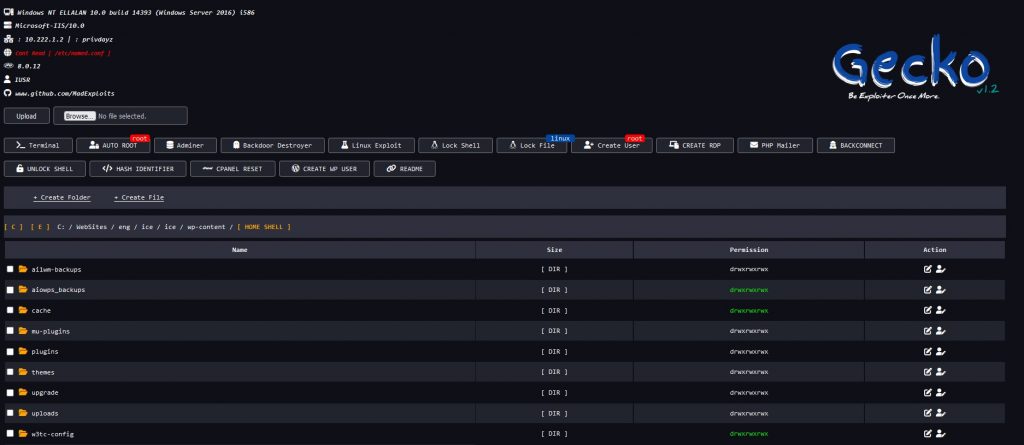
The Gecko Web Backdoor is a cutting-edge tool designed to bypass various server restrictions while maintaining complete stealth and efficiency. With its license version, Gecko offers a wide range of advanced features tailored for penetration testing and system management.
Bypass Capabilities
- 403 Bypass: Seamlessly access restricted directories.
- 404 Bypass: Navigate hidden paths without detection.
- 500 Bypass: Handle internal server errors efficiently.
- LiteSpeed Bypass: Overcome LiteSpeed-specific restrictions.
- BlankPHP Bypass: Tackle blank PHP response challenges.
- Downloaded Bypass: Ensure smooth operations in limited environments.
Key Features
- Linux Exploit Suggester: Identify and exploit vulnerabilities in Linux systems.
- Backdoor Destroyer: Securely remove backdoors from compromised environments.
- Auto Root via PwnKit: Automate privilege escalation with PwnKit integration.
- File Locking Mechanism: Lock critical files and shells for added security.
- Add ROOT Edition User: Create administrator-level accounts effortlessly.
- Unlock Shell Access: Regain control with the unlock shell feature.
- Backconnect Functionality: Establish reverse connections for secure access.
- Hash Identifier: Decode and identify hash algorithms efficiently.
- Adminer Integration: Streamline database management with built-in Adminer.
- CPanel Reset: Reset CPanel credentials with ease.
- WordPress Admin Add: Add WordPress admin users instantly.
- Compressor & Decompressor Tools: Manage files with built-in ZIP and archive tools.
Undetectable Operations
Gecko is a no-detect shell that operates under the radar of antivirus and intrusion detection systems, ensuring stealthy operations across various platforms.
Elevate your penetration testing capabilities with the Gecko Web Backdoor. Its robust bypass mechanisms and comprehensive feature set make it an invaluable asset for cybersecurity professionals.