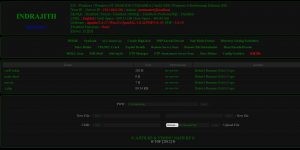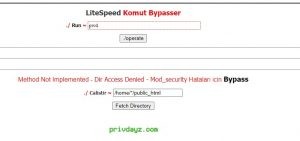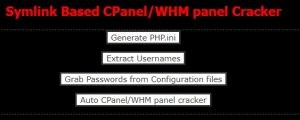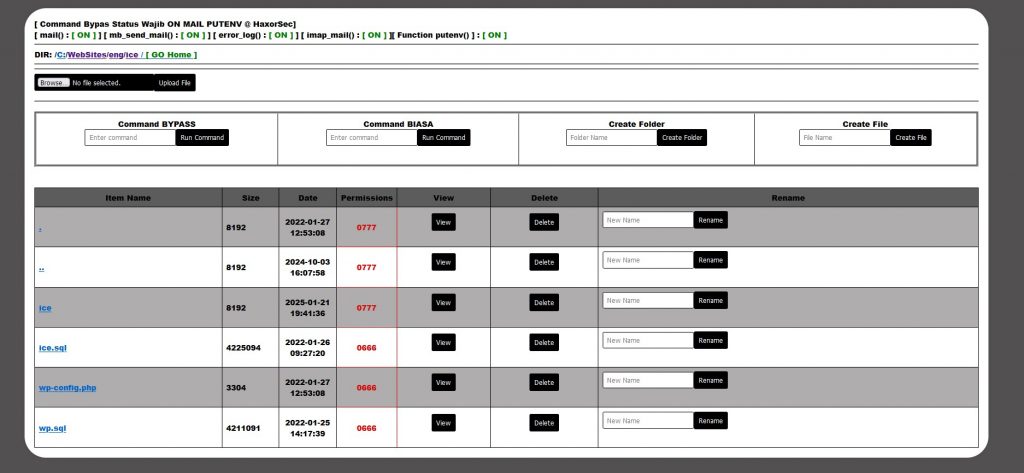
The BypassServ Mini Shell is a highly advanced backdoor webshell designed to evade detection by anti-virus systems such as ClamAV and VirusTotal. Engineered with cutting-edge bypass features, it leverages commands like mail(), mb_send_mail(), and others to effectively circumvent PHP’s disable functions. This makes it a powerful tool for individuals seeking stealth and efficiency in system access.
Features
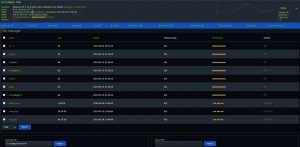
Command Shell
- Advanced bypass for commands including
mail()anderror_log() - Execute system-level commands with stealth and precision
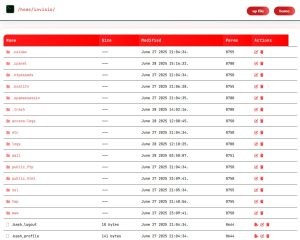
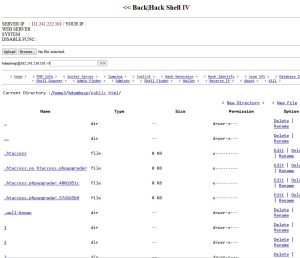
File Management
- Upload File: Easily upload files to the server
- Edit File: Modify file contents directly within the shell
- Create File: Generate new files for testing or deployment
- Rename File: Organize files with custom names
Directory Management
- Add Directory/Folder: Create new directories for better organization
Disclaimer
This tool is intended strictly for authorized security testing and educational purposes. Unauthorized use of this webshell is illegal and unethical. Always obtain proper permission before using this tool on any system.