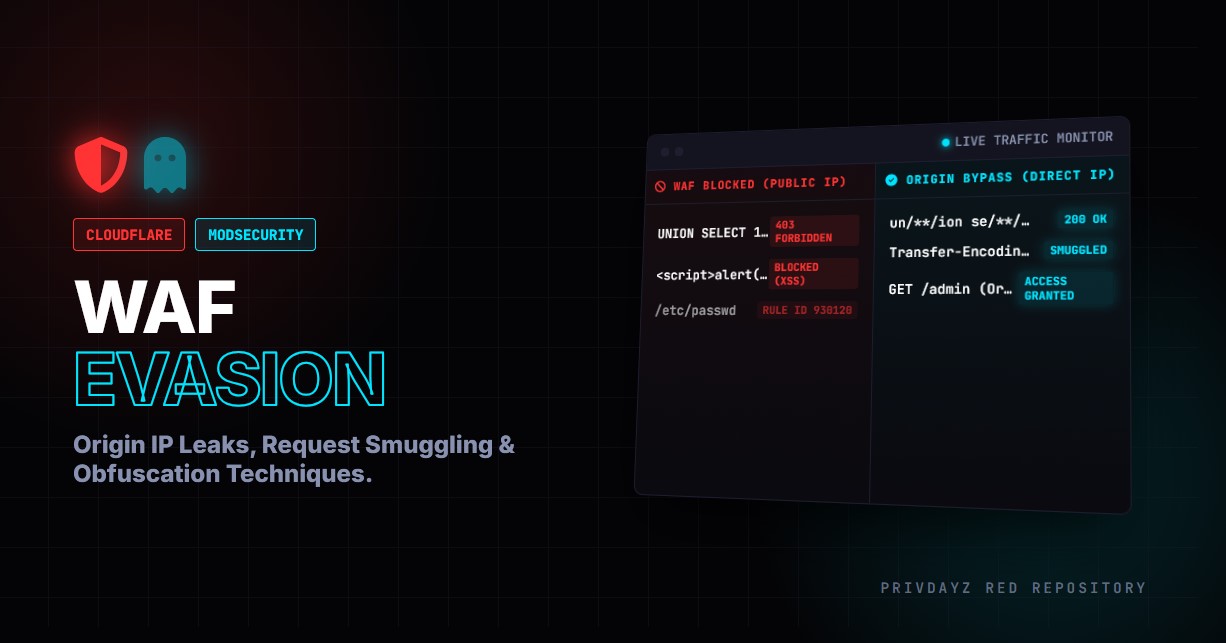
The modern web is no longer a direct line between a client and a server. It is a fortress. Standing at the gate of almost every high-value target is a Web Application Firewall (WAF). Whether it is the omnipresent Cloudflare, the rigid ModSecurity (OWASP CRS), or enterprise solutions like Akamai and F5, the WAF is the first line of defense designed to crush your payloads before they ever reach the application code.
For a Red Teamer, the WAF is not a wall; it is a filter. And like any filter, it has holes. It relies on signatures, rules, and known patterns. If you can make your malicious traffic look “normal,” or if you can find a side door that the WAF doesn’t guard, you win.
This comprehensive treatise explores the advanced methodology of WAF Evasion in 2026. We will move beyond simple script-kiddie tricks and delve into Origin IP exposure, HTTP Protocol Smuggling, and payload obfuscation techniques that render firewalls blind.
Operational Warning
Attempting to bypass a WAF on unauthorized infrastructure is a hostile act and is illegal under most cybercrime laws (CFAA, GDPR, etc.). WAF providers like Cloudflare log bypass attempts aggressively. This research is intended solely for authorized Penetration Testing and educational purposes.
1. The Architecture of Defense: How WAFs Think
To defeat the enemy, you must understand their logic. WAFs generally operate in two modes:
- Negative Security Model (Blacklisting): “Block known bad things.” This relies on Regex signatures (e.g., block requests containing
UNION SELECT). This is the weakness of ModSecurity. - Positive Security Model (Whitelisting): “Allow only known good things.” Much harder to bypass, but rare due to high maintenance.
Cloudflare adds a third layer: Behavioral Analysis. It challenges the client (JavaScript puzzles) to ensure it’s a real browser, not a bot like curl or sqlmap.
2. Strategy A: Direct IP Attacks (The “Side Door”)
The most effective way to bypass a WAF is not to interact with it at all. Cloudflare acts as a Reverse Proxy. It sits in front of the real server.
User -> Cloudflare (WAF) -> [Protection] -> Origin Server (Real IP)
User ———————> [No Protection] -> Origin Server (Real IP)
If you can find the Real IP (Origin IP) of the server, you can send your SQLi/XSS payloads directly to that IP, bypassing Cloudflare entirely. Here is how we hunt for it.
2.1. Historical DNS Records
Websites often start without Cloudflare. Their old DNS records (A Records) might still point to the same server IP. Services like SecurityTrails or ViewDNS.info archive these records.
2.2. Censys & Shodan Hunting
We can use Censys to scan the entire internet for SSL Certificates that match our target domain.
# Search for the specific SSL certificate
services.tls.certificates.leaf_data.names: “target.com”
# Filter out Cloudflare IPs
and not services.port: 80
If you find an IP like 1.2.3.4 serving the SSL certificate for target.com, edit your /etc/hosts file to point the domain to that IP and attack freely.
2.3. MX Records & Subdomains
Developers often protect the main domain (`www.target.com`) but forget the mail server (`mail.target.com`) or development subdomains (`dev.target.com`). If these subdomains are hosted on the same server but are not proxied (Gray Cloud in Cloudflare settings), pinging them reveals the real IP.
# Check if mail server leaks the IP
dig +short MX target.com
ping mail.target.com
3. Strategy B: Protocol Manipulation (Smuggling & Encoding)
If you cannot find the Origin IP, you must fool the WAF into thinking your malicious packet is harmless.
3.1. HTTP Request Smuggling (CL.TE / TE.CL)
WAFs and Backend Servers sometimes interpret the length of a request differently (Content-Length vs. Transfer-Encoding). We can hide a malicious request inside a benign one.
Imagine the WAF sees one safe request, but the backend server sees two: the safe one, and your smuggled payload. This completely bypasses inspection because the WAF never “saw” the second request logic.
3.2. Chunked Transfer Encoding
WAFs are optimized for speed. They often check only the first few kilobytes of a request. By using Transfer-Encoding: chunked, we can fragment our SQL injection payload into tiny pieces.
POST /login.php HTTP/1.1
Host: target.com
Transfer-Encoding: chunked
4
user
5
=admi
1
n
0
The WAF sees “user”, “=admi”, “n” as separate meaningless chunks. The backend server reassembles them into user=admin.
3.3. HTTP Parameter Pollution (HPP)
How does the WAF handle duplicate parameters?GET /search?q=safe&q=malicious
- WAF: Checks the first `q=safe`. Approved.
- ASP.NET Backend: Concatenates both.
- PHP Backend: Takes the last one (`q=malicious`).
By understanding the backend technology, we can slip payloads past the WAF’s inspection logic.
4. Strategy C: Obfuscation Techniques (ModSecurity Bypass)
ModSecurity with the OWASP Core Rule Set (CRS) relies heavily on Regex. If we break the Regex pattern, we break the defense.
4.1. SQL Injection Obfuscation
Standard payload: UNION SELECT 1,2,3 (Blocked instantly).
Bypass Techniques:
- Inline Comments:
UN/**/ION SE/**/LECT - Whitespace Manipulation:
UNION%0ASELECT(using Newline instead of Space) - Scientific Notation (MySQL):
UNION SELECT 1.0,2.0 - Version Comments:
/*!12345UNION*/ SELECT
4.2. XSS (Cross-Site Scripting) Obfuscation
Standard payload: <script>alert(1)</script> (Blocked).
Bypass Techniques:
- SVG OnLoad:
<svg/onload=alert(1)> - JavaScript Schemes:
<a href="javascript:alert(1)">Click</a> - Unicode Encoding: Using
\u0061instead ofa. - Double URL Encoding:
%253Cscript%253E
Pro Tip: Automation
Don’t do this manually. Use tools like WAFNinja or SQLmap’s --tamper scripts to fuzz the WAF and find which characters are allowed.
5. Strategy D: Case Switching & Uninitialized Variables
Sometimes, the rules are too specific. For example, a WAF might block /etc/passwd.
5.1. Bash Globbing & Variables
If you have a Remote Code Execution (RCE) vulnerability but the WAF blocks specific commands:
- Blocked:
cat /etc/passwd - Bypass:
cat /etc/pa??wd(Using wildcards) - Bypass:
cat /e${u}tc/pas${u}swd(Using uninitialized empty variables in Bash)
The WAF sees random garbage characters, but the Linux kernel ignores the empty ${u} variables and executes the command perfectly.
6. Tooling: The WAF Hunter’s Arsenal
Professional auditing requires professional tooling. Here is the Red Team standard for 2026.
# 1. Wafw00f – Identify the WAF
wafw00f https://target.com
# 2. CloudFail – Hunt for Origin IPs using misconfigurations
python3 cloudfail.py –target target.com
# 3. Bypass-Firewalls-by-DNS-History
./bypass-firewalls-by-dns-history.sh -d target.com