Author: BloodSword
Platform: Windows Server (IIS, ASP Classic), All Modern Windows OS
Disclaimer: This content is for educational and penetration testing purposes only. Unauthorized use is illegal!
What is AspRootkit 1.0?
AspRootkit 1.0 by BloodSword is a next-generation web shell & rootkit designed for absolute control over Windows-based web servers. Developed by the infamous BloodSword, this tool is engineered for red-teamers, exploit researchers, and underground hackers who require stealth, flexibility, and advanced privilege escalation techniques.
Unlike generic shells, AspRootkit integrates multiple bypass mechanisms and persistence modules, making it a weapon of choice for post-exploitation, advanced lateral movement, and full server takeover.
Core Features
- Multi-Method Admin Creation: Adds new admin users with
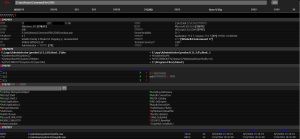
net user,net localgroup,PowerShell,WMIC,SCHTASKS,SC.EXEand other bypass techniques. - Interactive Command Execution: Execute Windows commands (cmd.exe, PowerShell) and get live output, including background tasks and scheduled jobs.
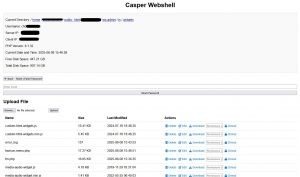
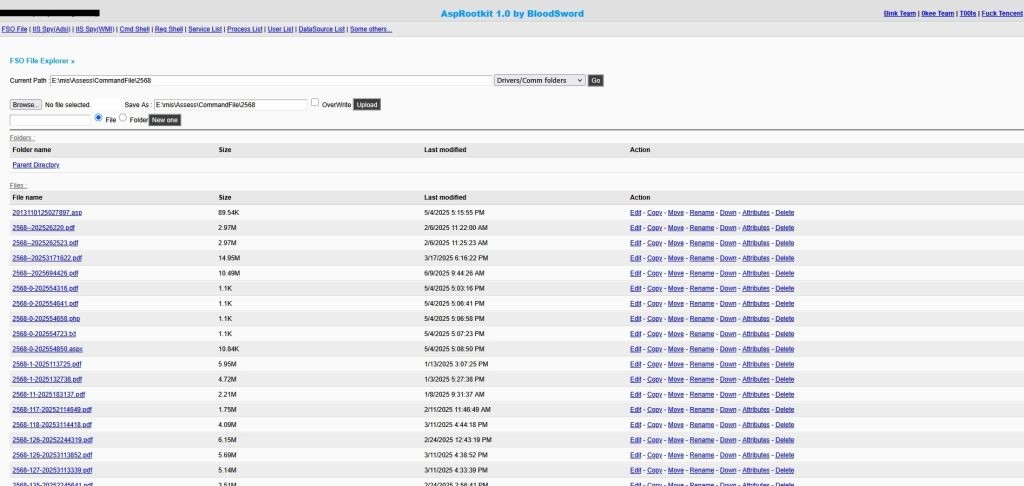
- File Management: Upload, download, edit, move, copy, and delete files or directories anywhere on the server—built-in FSO & ActiveX bypass.
- Persistence Toolkit: Install autoruns, backdoors, registry keys, and hidden users for long-term access—even after reboot.
- Registry & System Control: Direct registry editing, privilege escalation, RDP/3389 enable, user enumeration, and group policy hacking.
- Anti-Forensics & Stealth: Logs cleaner, rootkit-style hiding, custom obfuscation (Unicode, base64, XOR), anti-antivirus tricks, and process injection modules.
- Bypass Everything: Works on most shared/VDS/dedicated servers. Can evade web application firewalls (WAF) and classic AV signatures with polymorphic code.
- CTF & Red Team Ready: Built for penetration testers, bug bounty hunters, and security researchers looking for real-world exploitation practice.
Tools & Modules Included
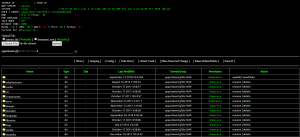
- CMD/PowerShell Console: Fully interactive command shell with real-time output.
- Admin User Creator: Tries every known privilege escalation and user add method—auto-selects the working one.
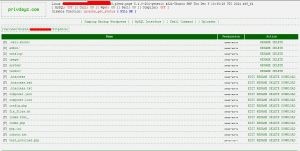
- File Explorer: Browse, search, and manage files on all drives—including system32 and protected folders.
- Persistence Installer: Installs registry run keys, scheduled tasks, service-level backdoors, and hidden startup scripts.
- Network Scanner: Scan open ports, enumerate local users, list services and processes, check AV/firewall status.
- Database Shell: Run direct queries via MS SQL Server xp_cmdshell and other DB engines.
- Web Upload & Download: Remote file dropper (HTTP/HTTPS) for lateral movement or C2 ops.
- Obfuscation Engine: Every payload is obfuscated and optionally encrypted with custom routines.
- Custom Plugins: Easy to add custom VBScript/JS/ActiveX code as “plug-ins” for special missions.
Why is AspRootkit 1.0 Different?
Most web shells are basic and get blocked within seconds by modern security tools. AspRootkit 1.0 leverages multi-stage persistence, privilege escalation chains, and failsafe admin creation. Even if classic methods fail (access denied, restricted group policies, locked down environments), the shell auto-switches to lesser-known Windows “LOLBAS” tricks, like abusing at.exe, bitsadmin, wmi, or crafting malicious registry scripts.
Every command, every attempt is fully logged in the output, so you know which method worked. For maximum stealth, it can self-destruct or hide itself after deployment.
Usage & Warnings
Warning: This shell is for advanced operators only. All code is for research and authorized penetration testing in lab or legal environments. Any illegal use is strictly forbidden and can be prosecuted.
TL;DR: Priv8. Fast. Undetectable. If you want to own the box, AspRootkit 1.0 by BloodSword is the ultimate Swiss army knife for ASP exploitation in 2025.
Need the code or a custom version? Join Privdayz Underground. Stay l33t.
# Usage Example: - Upload aspRootkit1.0.asp to any writable folder. - Access via browser, log in, run Multi-Method Admin Adder. - If any method works, you'll see "User added: username / password". - Use File Explorer, Registry Editor, and other tools for full pwnage.